Grammatically Gnosis is a Greek noun for knowledge. In the English language, Gnosis generally refers to the word’s meaning within the spheres of Christian mysticism, Mystery religions, and Gnosticism, where it signifies a ‘spiritual knowledge or religion of knowledge, in the sense of mystical enlightenment or ‘insight.’
If we type “gnosis-safe.io” in the address bar of our browser, and the address leads us to a web page that claims,” The most trusted platform to manage digital assets on Ethereum.”
Introduction
Almost all people involved in Digital assets such as cryptocurrencies and NFTs use different types of crypto wallets in two main classes, hot wallets, and cold wallets. Hot wallets usually have a password; on some devices, they unlock biometrically or with fingerprints.
For more security in case of stealing the device or any other reasons that access to the wallet is banned, users can use 12 private phrases to reenter their wallets. Still, for institutional digital assets, it is not the security that satisfies all beneficiaries. There must be a multi-signature crypto wallet, and the Gnosis wallet is a solution.
Risks of Ordinary Hot Wallets
Most people who hold cryptocurrencies use a single key wallet, often called an EOA (Externally Owned Account). 12-word private keys are the highest level of security. The privacy that ordinary EOAs can offer their users is good but doesn’t seem enough because the funds can be stolen if exposed to private keys. Most businesses have more than one founder, who might not like their assets under a single person’s control. There always is the risk of stealing funds if the authorized person accidentally exposes private keys or decides to defalcate digital assets.
What is Gnosis Safe?
Gnosis Safe is a smart contract wallet operating on Ethereum that needs a minimum number of authorized people to approve a transaction before it can occur (M-of-N). On top of that, Gnosis Safe gives its users complete self-custody over their assets.
Steps we must take to occur a transaction using the Gnosis wallet. Gnosis Safe backs an assortment of signer wallets, but the most popular options are Metamask and hardware wallets such as Trezor and Ledger. However, it is the Gnosis team’s recommendation, and interested users should investigate what wallets meet their needs and preferences.

How Many Authorized People?
Since more than one person should have access, there must be more than one owner account to manage funds as a group. Then always, more than one authorized person must own the Gnosis Safe Wallet to have more than one authentication factor, even if an individual manages funds. The Gnosis Safe team recommended using a threshold higher than one because no single account can execute transactions alone.
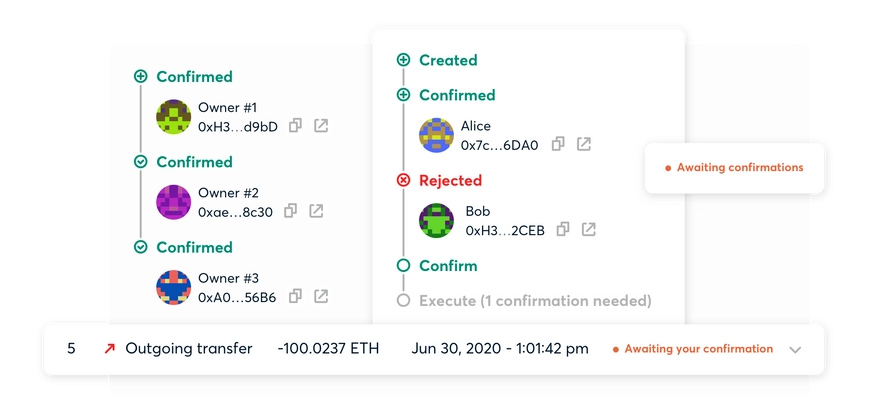
There should always be at least one more account to verify and permit Safe execution transactions. If an attacker successfully controls one of the authorized accounts, they cannot move funds alone. If an owner loses access to their account, the system doesn’t lock users automatically, and other owners can still execute transactions.
What is a Safe Transaction Hash (safeTxHash) in Gnosis Safe?
Similar to the regular transaction hash, we use “safeTxHash,” to identify a transaction of a specific Safe. It is computed based on the Safe address, transaction destination, Safe nonce, and data. The “safeTxHash” is the method owners of a Safe use to sign to confirm transactions.
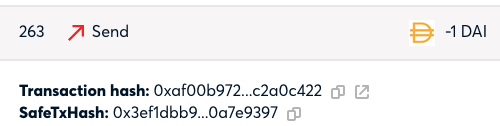
By signing this specific hash, parties to a transaction authorize the transaction that resulted in this particular hash. As “safeTxHash” is unique, there are no two different Safe transactions that result in the same “safeTxHash” on the same network. (Technically, it’s not impossible, but very unlikely in a way that this is negligible.) Gnosis claims.
Users need the full Safe transaction parameters to figure out the “safeTxHash,” and then it is unattainable to emanate the details based on the “safeTxHash.”
According to the Gnosis Dafe, there are three options to dine SafeTXHash,
- Option 1: Open the transaction details on the web. There is the Ethereum transaction hash as well as the “safeTxHash.”
- Option 2: Users can open their Safe in the Safe mobile app, go to transaction details, and then “advanced,” it is there.
- Option 3 (technical): Calculate it by calling” TransactionHash” on the user’s Safe.
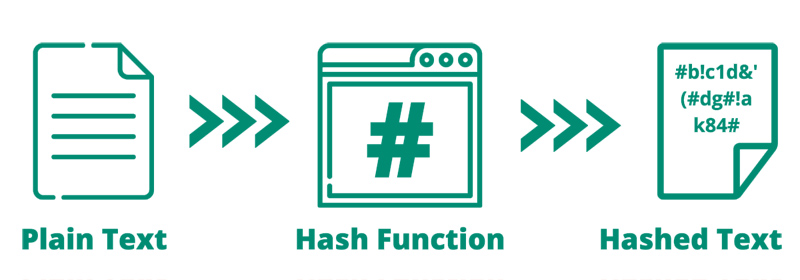
What is a HASH?
A hashing algorithm is an algorithm that produces a fixed-length output based on a variable length input, and it should not be possible to figure out the input based on the output hash. In addition, no two inputs result in the same output.
Is It Possible Always To Use The Regular Transaction Hash?
Possibly not because both methods are to accomplish different use cases;
- The regular transaction hash differs because it depends on what account submits the transaction. All accounts can submit Safe transactions as long as the signatory signatures are valid. If users use the regular transaction hash, then this method will not work.
- SafeTxHash takes data such as gas tokens into account. Using this method doesn’t work for a regular transaction and therefore is not reflected in a regular transaction hash.
- There could be numerous Safe transactions within a single Ethereum transaction, so if users use the regular transaction hash instead of safeTxHash, it would not be possible to identify a Safe transaction anymore uniquely.
Signatures in Gnosis Safe
The Safe supports different types of signatures. Gnosis Safe website says that all ll signatures are combined into a single byte and transmitted to the contract when a transaction should execute.
Each signature has an unchanging length of 65 bytes. Suppose it is necessary to provide more data. In that case, the additional data adds to the end of concatenated constant data of all signatures, and finally, the positions encode and add to the regular length data.
What is a Hash validator?
The Safe keeps track of all pre-validated hashes. “It happens with a mapping address to the mapping of bytes32 to boolean where it is possible to set a hash as validated by a certain address (hash validator)”.
The system uses “ApproveHash” to add an entry to this mapping. Conversely, if the validator is the same as the sender of the transaction that has executed the Safe transaction, using ApproveHash to add an entry to the mapping is not required anymore.
For more information, please visit https://docs.gnosis-safe.io/contracts/signatures
Conclusion
Gnosis Safe is a solution for those who want to manage funds that belong to a business with more than an authorized person in digital assets that must hold in a crypto wallet. Gnosis provides a good option for institutions and makes the blockchain-safe ecosystem safer. To understand this case better, suppose a hacker or a fudge employee wants to embezzle the crypto assets of the institution. In that case, they can’t make that transaction occur because more authorized people must approve to perform the transaction to transfer funds from the Gnosis Safe wallet to the destination account.
